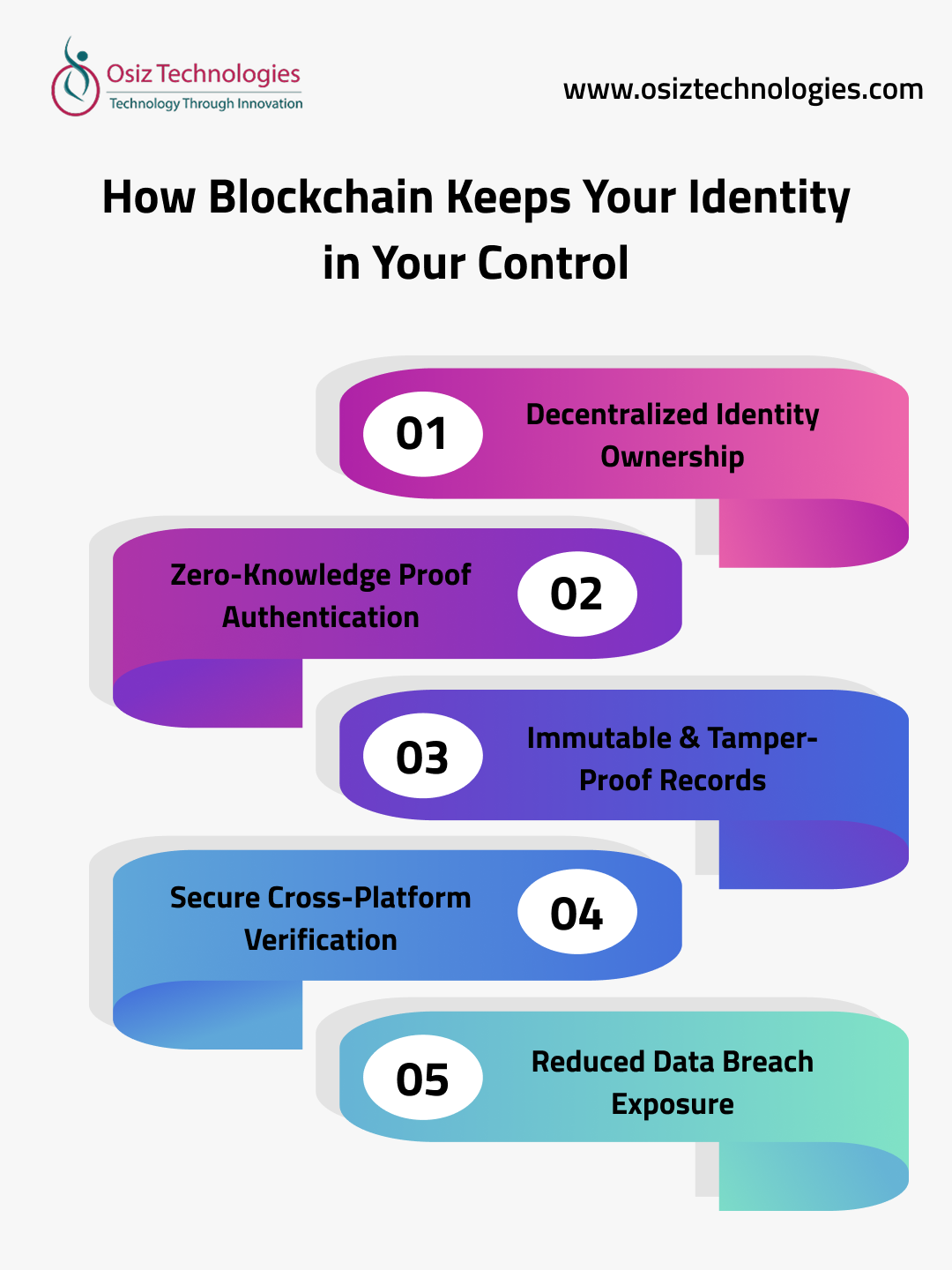
Smart Digital Tools Improving Everyday Workflow and Online Data Security for Everyone
The Growing Need for Efficient Online Tools
Modern digital tasks often involve working with large files, complex data, or sensitive online accounts. Individuals and professionals increasingly search for easy solutions that simplify processes and protect information. From organizing code to enhancing cybersecurity practices, the right tools make everyday digital activity faster and safer. This article discusses how essential online utilities are changing productivity and why choosing reliable platforms matters.
Using Tools That Simplify Data Structure
One helpful tool for managing code and data records is an xml formatter. This solution helps users clean, structure, and visually format XML files in a readable way, especially when the data becomes complex. An xml formatter saves time by automatically aligning tags and highlighting errors that might otherwise go unnoticed. This improves accuracy, reduces confusion, and supports error-free data processing. Developers and students working with XML files can experience smoother workflows by using such tools regularly.
Enhancing Digital Accuracy with Smart Utilities
Online work often requires precise formatting and validation. Tools that support proofreading, correcting code, and converting data formats reduce the risk of mistakes. Whether someone handles documentation, works on a software project, or prepares data to share with colleagues, accuracy contributes to both professionalism and efficiency. These utilities encourage error-free results without requiring advanced technical skills.
Easy Accessibility and Time-Saving Solutions
Digital tools offering online access save time and improve convenience. Instead of installing heavy software, users can open a browser and complete tasks instantly. The ability to handle work smoothly from any device boosts productivity. This adds value for people working remotely, learning through online courses, or managing personal records from home.
Protecting Online Accounts with Secure Password Practices
Security is another crucial part of daily digital activity. A strong password reduces the risk of unauthorized access. Tools like a Random Password Generator create complex passwords that are difficult for attackers to guess. When a Random Password Generator supports encryption-friendly characters and length customization, it boosts overall safety for emails, banking apps, and personal accounts. Such tools encourage users to follow better security habits without extra effort.
Conclusion: Embracing Smart Digital Tools for Better Productivity and Security
Digital life becomes easier when tools help organize data efficiently and protect information from online threats. Formatting solutions enhance clarity and order, while password-generating utilities improve safety in everyday browsing. These technologies make online tasks simple, accessible, and secure. As users continue to explore helpful platforms, Dev Tools Kit stands out for offering useful solutions that support both productivity and online protection. By adopting the right digital tools, anyone can manage information with confidence and complete work more effectively.
Smart Digital Tools Improving Everyday Workflow and Online Data Security for Everyone
The Growing Need for Efficient Online Tools
Modern digital tasks often involve working with large files, complex data, or sensitive online accounts. Individuals and professionals increasingly search for easy solutions that simplify processes and protect information. From organizing code to enhancing cybersecurity practices, the right tools make everyday digital activity faster and safer. This article discusses how essential online utilities are changing productivity and why choosing reliable platforms matters.
Using Tools That Simplify Data Structure
One helpful tool for managing code and data records is an xml formatter. This solution helps users clean, structure, and visually format XML files in a readable way, especially when the data becomes complex. An xml formatter saves time by automatically aligning tags and highlighting errors that might otherwise go unnoticed. This improves accuracy, reduces confusion, and supports error-free data processing. Developers and students working with XML files can experience smoother workflows by using such tools regularly.
Enhancing Digital Accuracy with Smart Utilities
Online work often requires precise formatting and validation. Tools that support proofreading, correcting code, and converting data formats reduce the risk of mistakes. Whether someone handles documentation, works on a software project, or prepares data to share with colleagues, accuracy contributes to both professionalism and efficiency. These utilities encourage error-free results without requiring advanced technical skills.
Easy Accessibility and Time-Saving Solutions
Digital tools offering online access save time and improve convenience. Instead of installing heavy software, users can open a browser and complete tasks instantly. The ability to handle work smoothly from any device boosts productivity. This adds value for people working remotely, learning through online courses, or managing personal records from home.
Protecting Online Accounts with Secure Password Practices
Security is another crucial part of daily digital activity. A strong password reduces the risk of unauthorized access. Tools like a Random Password Generator create complex passwords that are difficult for attackers to guess. When a Random Password Generator supports encryption-friendly characters and length customization, it boosts overall safety for emails, banking apps, and personal accounts. Such tools encourage users to follow better security habits without extra effort.
Conclusion: Embracing Smart Digital Tools for Better Productivity and Security
Digital life becomes easier when tools help organize data efficiently and protect information from online threats. Formatting solutions enhance clarity and order, while password-generating utilities improve safety in everyday browsing. These technologies make online tasks simple, accessible, and secure. As users continue to explore helpful platforms, Dev Tools Kit stands out for offering useful solutions that support both productivity and online protection. By adopting the right digital tools, anyone can manage information with confidence and complete work more effectively.