Level 1 & Level 2 CMMC Checklist: The Post-Implementation Guide
Most business owners are panic-buying software right now. They are wrong.
Compliance isn't a product; it’s a paper trail. You can buy the most expensive firewall on earth, but if you don't have a System Security Plan (SSP) that references it, you will fail an audit.
This isn't a theoretical guide. This is a forensic triage checklist. We are going to walk through the 12 steps you need to take today to stop the bleeding and secure your revenue.
Phase 1: Immediate Triage (The "Must-Haves")
Before you spend a dime on consultants, you need to stop and look at the map. Most companies fail because they try to secure everything. That is a bankruptcy strategy.
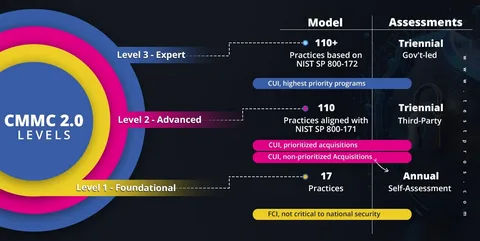
1. Identify Your Contract Level
Go to your contracts manager. Pull your active DoD contracts. Look for these clauses:
-
FAR 52.204-21: This means you handle Federal Contract Information (FCI). You need Level 1 (17 Controls).
-
DFARS 252.204-7012: This means you handle Controlled Unclassified Information (CUI). You need Level 2 (110 Controls).
If you only have FCI, stop reading about encryption keys. Focus on the basics. If you have CUI, you have a mountain to climb.
2. Define the "CUI Enclave" (Scoping)
This is the most critical step for your budget. Do not try to make your entire company CMMC compliant. It is too expensive. Instead, build a "Secure Enclave."
-
Identify exactly where CUI flows (email, file server, ERP).
-
Segregate that data from your HR, Marketing, and Sales departments.
-
Action: Create a network topology diagram that draws a bright red line around your CUI assets. Only the assets inside the line get the expensive security treatment.
3. Calculate Your Preliminary SPRS Score
You need to know how bad the situation is.
-
Start at 110 points.
-
Subtract 5 points for every "Significant" control you miss (like MFA).
-
Subtract 3 points for "Specific" controls.
-
Subtract 1 point for "Basic" controls.
-
Reality Check: Most small businesses start with a score of -27. Yes, negative scores are possible (down to -203). Be honest. Fraud is worse than a low score.
Phase 2: Documentation (The "Paperwork" Phase)
Auditors don't trust what they see; they trust what they read. If it isn't written down, it didn't happen.
4. Build the System Security Plan (SSP)
This is your defense in court. The SSP is a living document that describes how you meet every single requirement.
-
Checklist Item: Does your SSP list the hardware model, software version, and responsible person for every control?
-
Warning: A "template" SSP that you haven't customized is an automatic failure.
5. Create the Plan of Action & Milestones (POA&M)
You aren't perfect. The DoD knows this. The POA&M is your "fix-it" list. It lists every gap you found in Step 3.
-
Checklist Item: Assign a realistic due date and a budget for every item.
-
Critical Rule: You generally cannot use a POA&M for "High Risk" controls like missing antivirus. You just have to fix those.
6. The Shared Responsibility Matrix (SRM)
If you use Microsoft 365, AWS, or an MSP, you need this document. It defines who does what.
-
Checklist Item: Create a matrix with these exact columns:
-
Control ID (e.g., AC.L2-3.1.1)
-
Provider Responsibility (What Microsoft does)
-
Customer Responsibility (What YOU do)
-
Shared Responsibility (Where you overlap)
-
If you need help building these documents, consider professional CMMC compliance services.
Phase 3: Technical Implementation (The "Hardening" Phase)
Now we get to the "widow-makers"—the technical controls that trip up 80% of companies.
7. Access Control (AC) Checklist
-
Multi-Factor Authentication (MFA): Implement this on everything. VPNs, cloud email, and crucially, local administrator access.
-
Session Locks: Configure screens to lock after 15 minutes of inactivity.
-
External Connections: Verify that your firewall blocks all traffic by default and only allows specific, authorized connections.
8. Identification & Authentication (IA) Checklist
-
Complex Passwords: Enforce 12+ characters.
-
FIPS 140-2 Validated Encryption: This is the big one.
-
The Trap: "FIPS Compliant" is not the same as "FIPS Validated." You must use cryptographic modules that are on the NIST active validation list.
-
Action: Check your VPN and encryption software against the NIST CMVP database. If your module isn't there, you are non-compliant.
-
9. Audit & Accountability (AU) Checklist
-
Centralized Logging: You must collect logs from endpoints, firewalls, and servers.
-
Review Process: Assign a human to review these logs weekly. An automated tool collecting logs that nobody reads is useless.
-
Time Synchronization: Ensure all systems sync to a verifiable time source
10. Physical Protection (PE) Checklist
-
Visitor Logs: Maintain a physical or digital log of everyone who enters your facility.
-
Escort Policy: Non-employees cannot wander freely. They must be escorted.
-
Physical Keys: Track who has keys to the server room.
For a detailed breakdown of the costs associated with these tools, read our CMMC compliance cost breakdown.
Phase 4: The Human Factor
Your employees are your biggest risk.
11. Personnel Screening
-
Checklist Item: Run Tier 1 / Tier 3 background checks on all IT staff and anyone with access to CUI.
-
Foreign Nationals: Be extremely careful allowing non-US citizens access to CUI, especially if it is also export-controlled (ITAR).
12. Security Awareness Training
-
Checklist Item: Train staff on Insider Threats and Phishing.
-
Evidence: Keep the sign-in sheet. If you can't prove they took the training, they didn't take it.
Final Step: Submitting to SPRS
You have done the work. Now you must report it.
-
Log in to the PIEE (Procurement Integrated Enterprise Environment).
-
Access the SPRS module.
-
Enter your score (e.g., 85/110).
-
Enter the date of your assessment.
-
The Affirmation: A senior executive must sign off. This is a legal attestation. If you lie here, you are violating the False Claims Act.
If you are just starting out, use our CMMC Level 1 compliance checklist for a simpler entry point.
FAQ: Common Checklist Questions
Can I use a template for my SSP?
Yes, but you must customize it heavily. A "search and replace" job will be spotted by an assessor in five minutes.
What if my score is negative?
Submit it anyway. A negative score is better than no score. It shows you are honest and have a baseline. Then, use your POA&M to improve it rapidly.
Do I need a C3PAO for Level 2 right now?
It depends. For Phase 1, most contracts only require a Self-Assessment. However, the DoD can require a C3PAO assessment for high-priority contracts. Check your specific RFP.
Conclusion: Don't Let the Checklist Overwhelm You
The list is long, but the alternative is losing your business.
The DoD has moved from "Trust" to "Verify." This checklist is your tool to verify your own house before the government does it for you. Start with the "Must-Haves" in Phase 1. Define your scope. Protect your CUI.
You don't have to do it alone. If you need a gap analysis to fill this checklist accurately, Defend My Business is here to guide you. We help you navigate the chaos of cyber security compliance services and get you audit-ready.
- AI
- Vitamins
- Health
- Admin/office jobs
- News
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Spiele
- Gardening
- Health
- Startseite
- Literature
- Music
- Networking
- Andere
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness


